
Shruthi Shetty
Chief Information Officer, Technomers
Medium-scale enterprises often struggle with managing numerous devices, ensuring robust security, and achieving compliance with regulations.
These challenges lead to increased operational costs, frequent security breaches, and difficulty in maintaining customer trust.

Frequent security breaches compromise sensitive data, damaging trust.
High costs and complexity make achieving ISO, SOC2 and GDPR compliance difficult.
Managing multiple tools increases operational costs and inefficiency.
complIT One encapsulates everything you need for comprehensive IT security and compliance in a single, streamlined package.
Designed for ease of use and robust protection,it ensures your enterprise stays secure and compliant without the hassle.

Slash compliance time and costs by 4x, simplifying compliance tasks for effortless execution.

Amplify productivity and cut operational costs by 2x with integrated solutions.
Enhance customer trust with advanced security to drive sales, fueling business expansion.
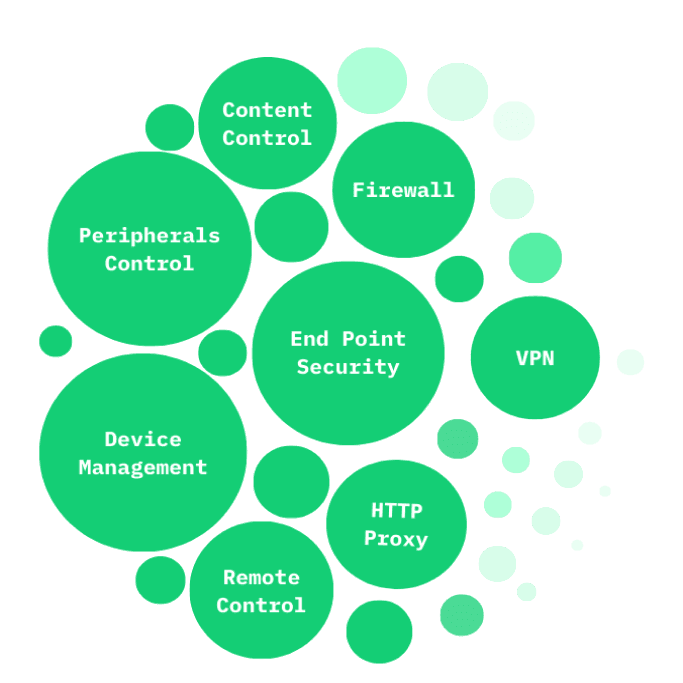
Endpoint Security provides advanced protection against malware, ransomware, and other cyber threats. It continuously monitors and defends all endpoint devices, ensuring they are secure and up-to-date.
Comprehensive threat detection and prevention.
Real-time monitoring and alerts.
Automatic updates to combat the latest threats.
Peripherals Access Control manages and secures the devices connected to your network. It prevents unauthorized devices from accessing your network and ensures that only approved peripherals are used.
Control over connected devices.
Prevention of unauthorized access.
Enhanced network security.
Device Management centralizes control of all your organization’s devices. It simplifies the management of configurations, updates, and security policies across all devices.
Centralized device control and management.
Simplified configuration and update processes.
Consistent security policies across all devices.
Content Control regulates and monitors the information accessed and shared within your organization. It helps prevent data leaks and ensures compliance with data security policies.
Monitoring and regulation of data flow.
Prevention of data leaks.
Compliance with data security policies.
HTTP Proxy secures web traffic and enhances browsing security. It filters malicious sites and content, ensuring safe and secure internet usage for employees.
Secure and filtered web traffic.
Protection against malicious websites.
Enhanced browsing security.
Remote Control provides efficient remote support and troubleshooting capabilities. It allows IT teams to access and resolve issues on employee devices from any location.
Efficient remote support and troubleshooting.
Reduced downtime and faster issue resolution.
Access to devices from any location.
Firewall protects your network from unauthorized access and cyber-attacks. It monitors and controls incoming and outgoing network traffic based on predetermined security rules.
Protection against unauthorized access.
Control over network traffic.
Defense against cyber-attacks.
Mobile Device Management (MDM) secures and manages mobile devices across your organization. It enforces security policies and ensures that mobile devices are compliant with organizational standards.
Secure management of mobile devices.
Enforcement of security policies.
Compliance with organizational standards.
VPN (Virtual Private Network) ensures secure and encrypted connections for remote workers. It protects data transmitted over the internet, keeping remote communications safe and private.
Secure and encrypted remote connections.
Protection of data in transit.
Enhanced privacy for remote work.
Integrates multiple IT security tools into one package, simplifying management and reducing costs.
Provides comprehensive protection against cyber threats, safeguarding sensitive company data.
Facilitates easier compliance with regulations like ISO, SOC2, and GDPR, reducing administrative overhead.
Automates routine IT management tasks, freeing up time for your team to focus on core business functions.
Adapts effortlessly to growing business needs, ensuring consistent protection as your enterprise expands.
Reduces overall IT expenses by consolidating essential security services, minimizing the need for additional investments.
Access to all 9 security tools
Free initial setup consultation
Continuous updates and upgrades
Platform/Data Migration support
24/7 customer support
Customizable security settings
/device/year
30 Days Money Back Guarantee
Support
About
Resources
Terms
Report
Privacy